Zyxel has been tracking the recent activity of threat actors targeting Zyxel security appliances and has released firmware patches to defend against it. Updates now available! Users are advised to install the patches for optimal protection.
Based on our investigation, the threat actors attempt to access a device through WAN; if successful, they then try to log in with stolen, valid credentials or bypass authentication, and to establish SSL VPN tunnels with existing or newly created users accounts, such as “zyxel_sllvpn”, “zyxel_ts”, or “zyxel_vpn_test”, to manipulate the devices’ configuration.
Zyxel has been collaborating with third-party security researchers to track the threat actors’ activities. Based on our investigation, they could be abusing a combination of attack vectors, including:
- Valid user credentials that they had previously harvested from the breach of past known vulnerabilities, potentially CVE-2020-29583 or CVE-2020-9054, were completely fixed in March and December 2020. We’ve observed the threat actors logging in using legitimate user-defined credentials with admin privileges, and in some cases, they also created new admin accounts.
- A newly uncovered authentication bypass vulnerability tracked as CVE-2021-35029, that did not properly sterilize input strings and could allow an adversary to gain access.
Affected Products:
VPN, ZyWALL, USG, ATP, USG FLEX Series in On-Premise Mode with remote management or SSL VPN enabled are vulnerable.
Those running the Nebula cloud management mode are NOT affected.
How to find out if your firewall is affected?
Affected Firmware Version:
ZLD V4.35 to ZLD 5.01
(date codes and weekly version user, please follow the Mitigation SOP] We are working on a weekly version that includes these fixes and release them separately as soon as possible.
Zyxel has released standard firmware patches that remain the definitive solution to the issues for the affected models, as listed in the table below. The patches also include additional security enhancements based on users’ feedback and security researchers’ advice, which we strongly recommend users install immediately for optimal network protection.
Thanks to the Spike Reply Cyber Security Team for working with us to investigate and fix this issue.
Firmware Patches
(You can use Online Firmware Update Service as the fastest way to upgrade the firmware)
How to upgrade USG devices via cloud-service
| Model | Download |
| All devices/All updates in one package | Download |
| USG FLEX 100 | Download |
| USG FLEX 100W | Download |
| USG FLEX 200 | Download |
| USG FLEX 500 | Download |
| USG FLEX 700 | Download |
| ATP100 | Download |
| ATP100W | Download |
| ATP200 | Download |
| ATP500 | Download |
| ATP700 | Download |
| ATP800 | Download |
| USG20-VPN | Download |
| USG20W-VPN | Download |
| USG40 | Download |
| USG40W | Download |
| USG60 | Download |
| USG60W | Download |
| USG110 | Download |
| USG210 | Download |
| USG310 | Download |
| USG1100 | Download |
| USG1900 | Download |
| USG2200 | Download |
| ZyWALL110 | Download |
| ZyWALL310 | Download |
| ZyWALL1100 | Download |
| VPN50 | Download |
| VPN100 | Download |
| VPN300 | Download |
| VPN1000 | Download |
Release Notes and Guidance Steps:
- CVE-2021-35029
Vulnerability fix for web-based management interface of Zyxel USG/ZyWALL, USG FLEX, ATP and VPN series
- Two-Factor Authentication Enhancement
Supports configurable 2FA service port.
[Object -> Auth. Method -> Two-Factor Authentication -> Authorized Port
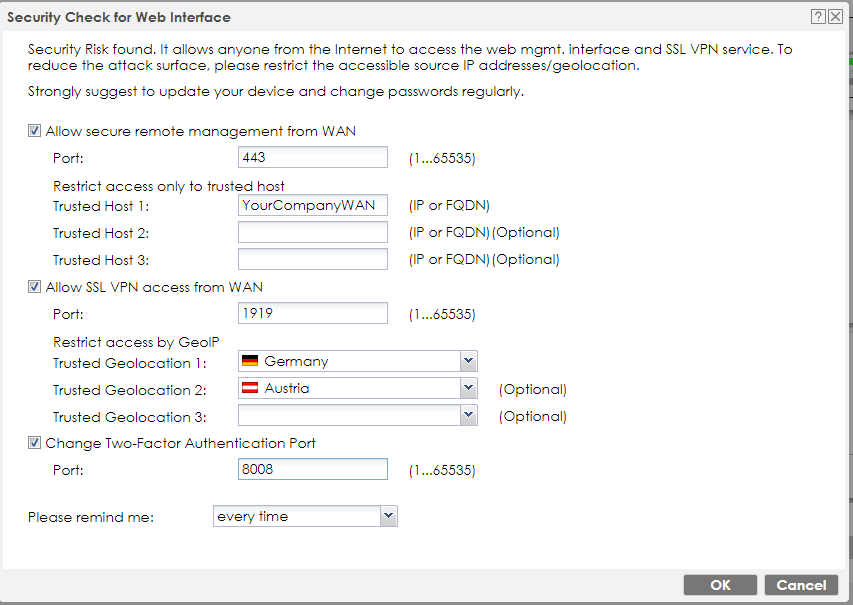
- Security Check Enhancement
Disables HTTP port automatically while allowing WAN management in security
check wizard.
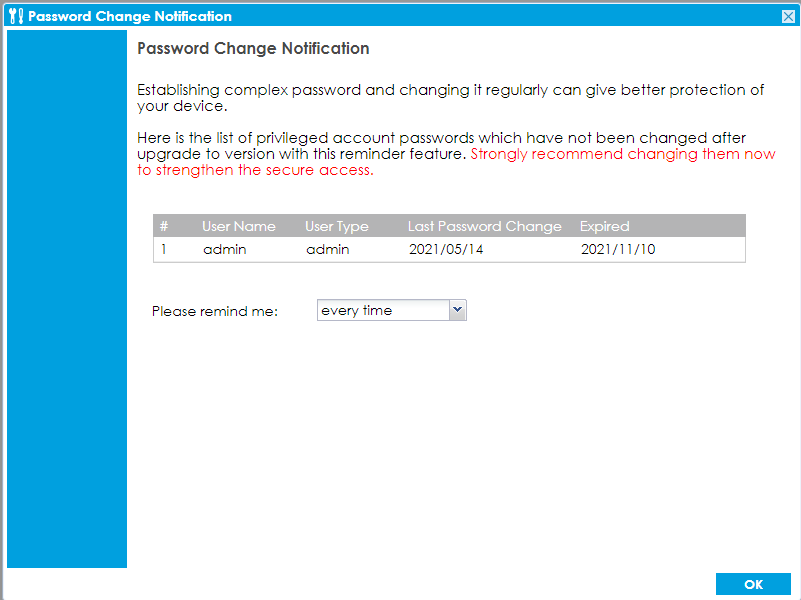
- Password Change Reminder
Reminds privileged accounts to change their passwords for security.
- Security Policy Check
Shows misconfiguration of security policies through a pop-up notification, along with firmware update and change password reminder.
The Security Check will pop up after the firmware update finish and the admin logs in to the device.
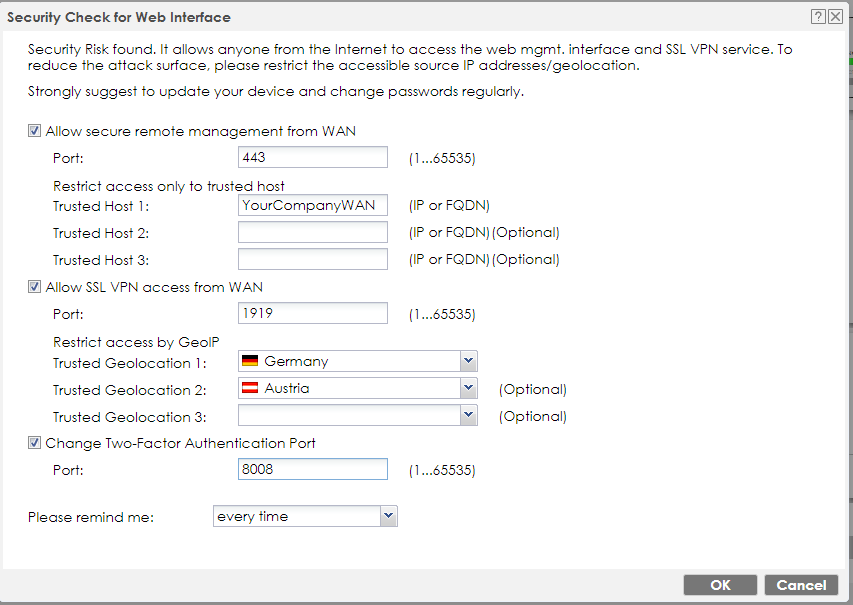
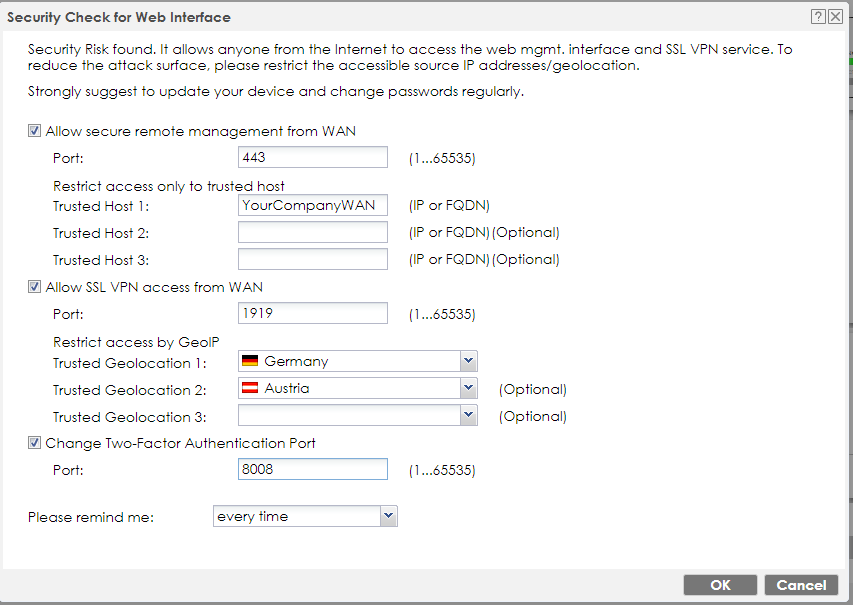
Preview Example of filled out Security Check for Web Interface
The WAN access should belong to your Company WAN IP/Admin only access IP.
The SSL VPN should belong to the free GeoIP feature, i.e. Germany and Austria. If this is the area, your SSL VPN workers will log in to the device. After creating this Security Check, you can add more IPs or countries by Firewall settings.
It's recommended to separate "SSL VPN Port" from "WAN Port for Admin Login", the VPN worker can, i.e. use Port 8443 to login with SSL VPN, where the Admin Login access is fully restricted.
If you are unsure about this step, click "Cancel" and follow the Mitigation steps below in this article.
- Log Enhancement
Provides a log history when the user object has been changed.
You can identify with the Category "User" and Syslog Server or an E-Mail Alert if a user has login/log out of your device or an admin user is created or deleted. Setting up a Syslog Server entry on a USG.
More enhancements:
- Initial Setup Wizard Enhancements
Helps users to enforce security policies against access to the web management interface and SSL VPN service from the Internet.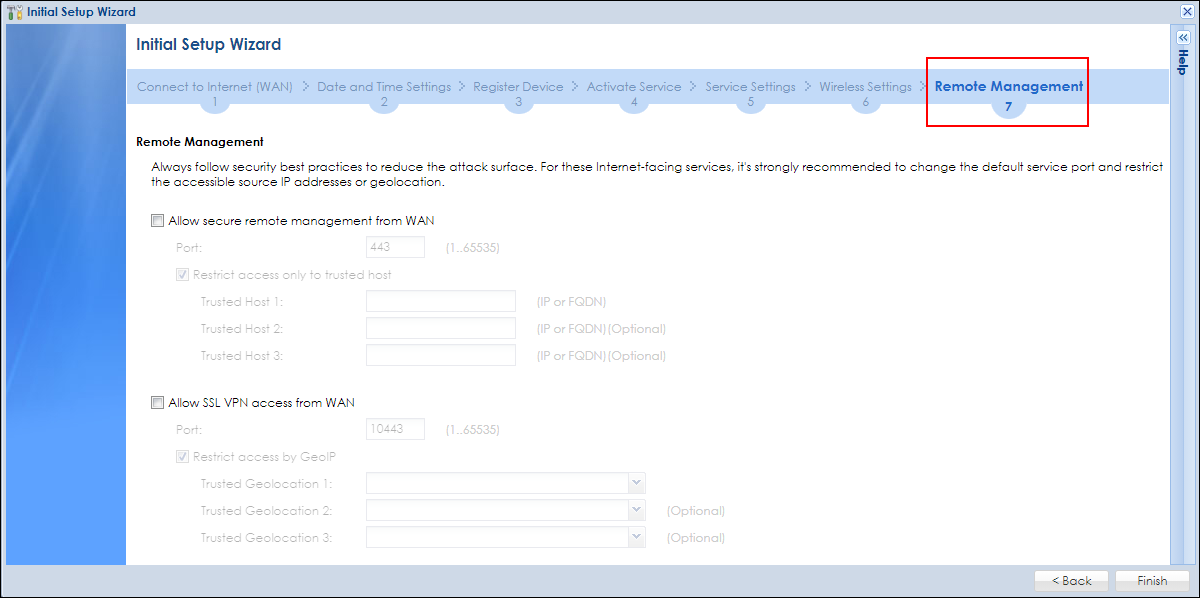
- Configurable SSL VPN and WAN Access
Separates access options on SSL VPN and WAN Access service.
How to use SSL VPN on a different port than the Web GUI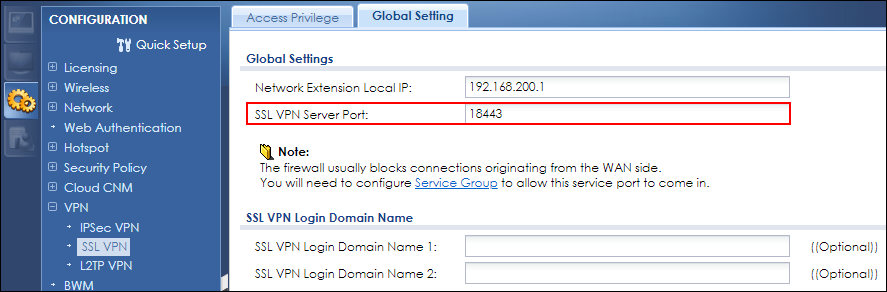
- GeoIP is now a Complimentary Feature.
Built-in GeoIP feature to strengthen security access-which is now available free of charge for the entire firewall range.
How to use the GeoIP feature
How to find out if your firewall is affected?
The following behaviour can potentially be a reason that you are affected:
- VPN Issues
- Routing Issue
- Traffic Issue
- Unknown Configuration parameters
- Additional Admin creation
One or multiple configuration changes shows up if your device is affected:
- Unknown Admin Accounts Created
[Configuration -> Object -> User/Group setting]
Fix Action: Delete all unknown Admin and User accounts
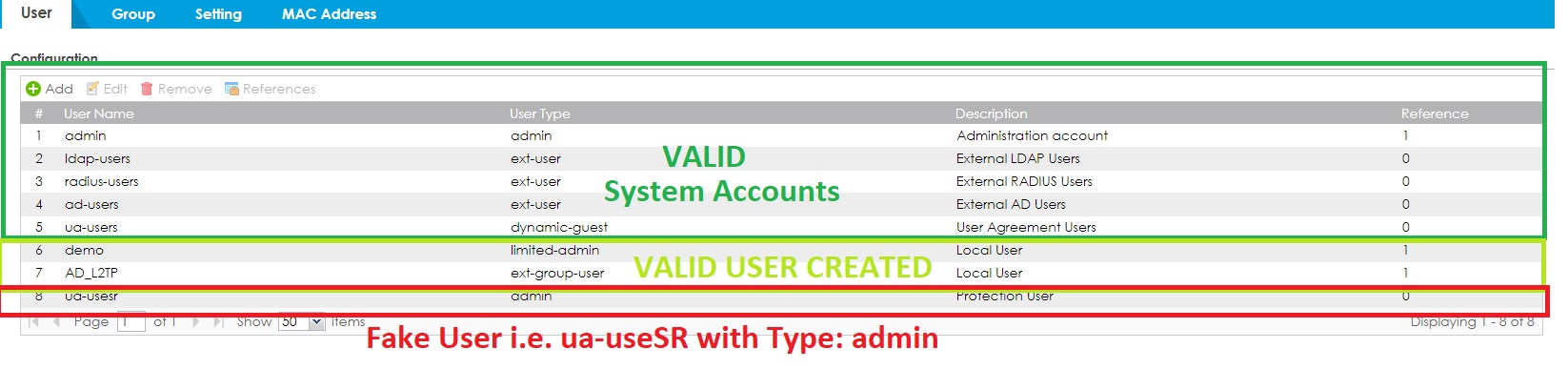
The User/Admin creation will be at the bottom (the last one in the list). Few examples could be:
(manage, zyxel_sllvpn, sslvpn_index, zyxel_ts, etc...) others/new unknown could happen too.
The accounts are usually at the bottom/last page of your account list.
- Unknown Policy Route created
[Configuration -> Routing -> Policy Route]
Fix Action: Delete Policy Route 1 if conditions matching
The Policy Route screen usually shows at position 1 an unknown Policy Route.
Example:
LAN1_Subnet -> to any -> Next-Hop -> AUTO
Example 2:
LAN1_Subnet -> to any -> Next-Hop -> VPN Tunnel - Unknown Secure Policy/Firewall Rule created
[Configuration -> Secure Policy]
Fix Action: Delete the firewall rule, showing "loseang" in the description.
A newly created firewall rule show up, with the description "loseang" and usually the way "WAN to ZyWALL". - Unknown SSL VPN Setup
[Configuration -> SSL VPN]
Fix Action: Delete the "SSL VPN" setup group/user
Typically a user named "zyxel_ts" or "zyxel_sllvpn" or "sslvpn_index" or "zyxel_vpn_test" is created and or this is the name of SSL VPN setup.
What can you do if you found the above mentioned points on your device?
1) Repair the device:
- Fix Action: Delete all unknown Admin and User accounts
- Fix Action: Delete Policy Route 1 if conditions matching
- Fix Action: Delete the firewall rule, showing "loseang" in the description
- Fix Action: Delete the "SSL VPN" setup group/user
2) Protect this device with the following changes and upgrade to the latest release firmware a
All protection changes are summarized in this video file:
a) Review the Firewall configuration (mandatory)
- Only allow Source IP, which is permitted to ZyWALL Zone Setup Assistance.
- Protect this with the GeoIP Country feature from your location Setup Assistance
- Make sure to set up all other not trusted connections from WAN to ZyWALL into a "deny" rule lower position as the allow rules.
b) Port Changes (suggest)
[Be careful - so modify Firewall first, and if you self connect by SSL VPN, it will reconnect you, don't block yourself]
- Change the port of HTTPS to another port. Setup Assistance
- Change the port for SSL VPN to another port which is not overlapping with HTTPS GUI Port
(ZLD 5.0 feature) Setup Assistance
c) Password changes (mandatory)
- Change the admin password
d) Setup 2-factor Login (optional) Setup Assistance
If you have any further questions or concerns about your network security, please contact our support team by submitting completing the support form here, or give us a call at 800-255-4101 option 5.
Comments
0 comments
Please sign in to leave a comment.