This guide will assist in the configuration of the IPSecuritas VPN Client (version 4.9.5) for VPN connectivity with Nebula CC IPSec Remote Access VPN feature.
Overview
A VPN (virtual private network) provides a secure communication between sites without the expense of leased lines. VPNs are used to transport traffic over the internet of any insecure network that uses TCP/IP communications. A remote access VPN (client-to-site) allows employees who are traveling or teleworkers, secure access to company network resources. There multiple types of VPN protocols/technologies, that can be used to establish a secure link to company network, L2TP, PPTP, SSL, OpenVPN, etc. This guide will reference the IPSec protocol to establish a secure VPN tunnel between external hosts (users connected to the internet outside the company network structure) and the NebulaCC gateway. Third party IPSec software is required to establish the VPN connection as current operating systems lack a built-in IPSec client. This walkthrough will help configure the VPN setup on the IPSecuritas VPN client (version 4.9.5).
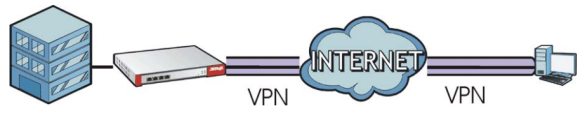
Supported Devices
NSG50
NSG100
NSG200
NSG300
Nebula CC VPN Setup
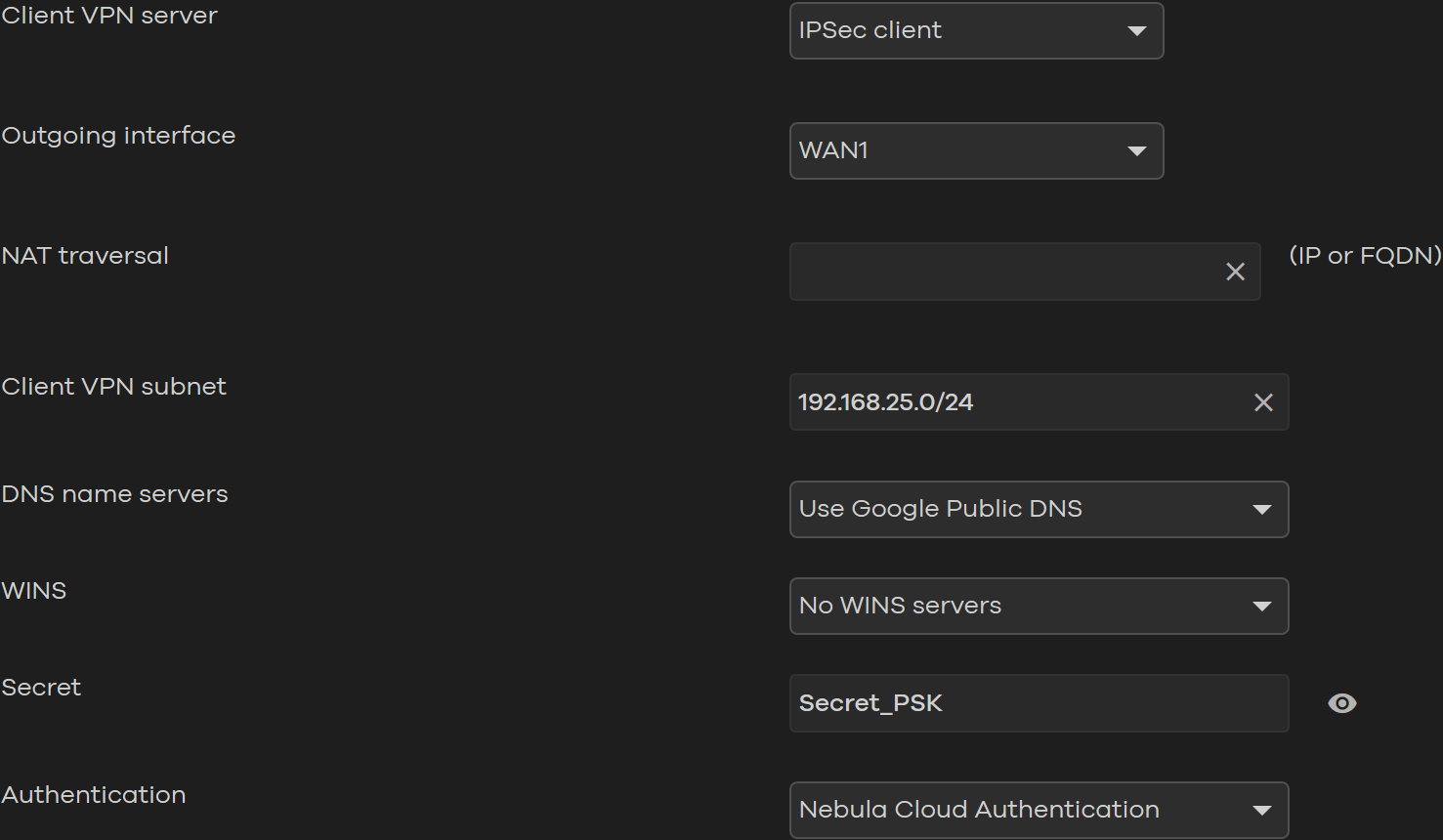
Click into the new Nebula CC user interface and go to Security gateway → Configure → Remote access VPN, specify the Client VPN server as IPSec client, if your NSG is located behind the NAT gateway, you will need to type NAT traversal.
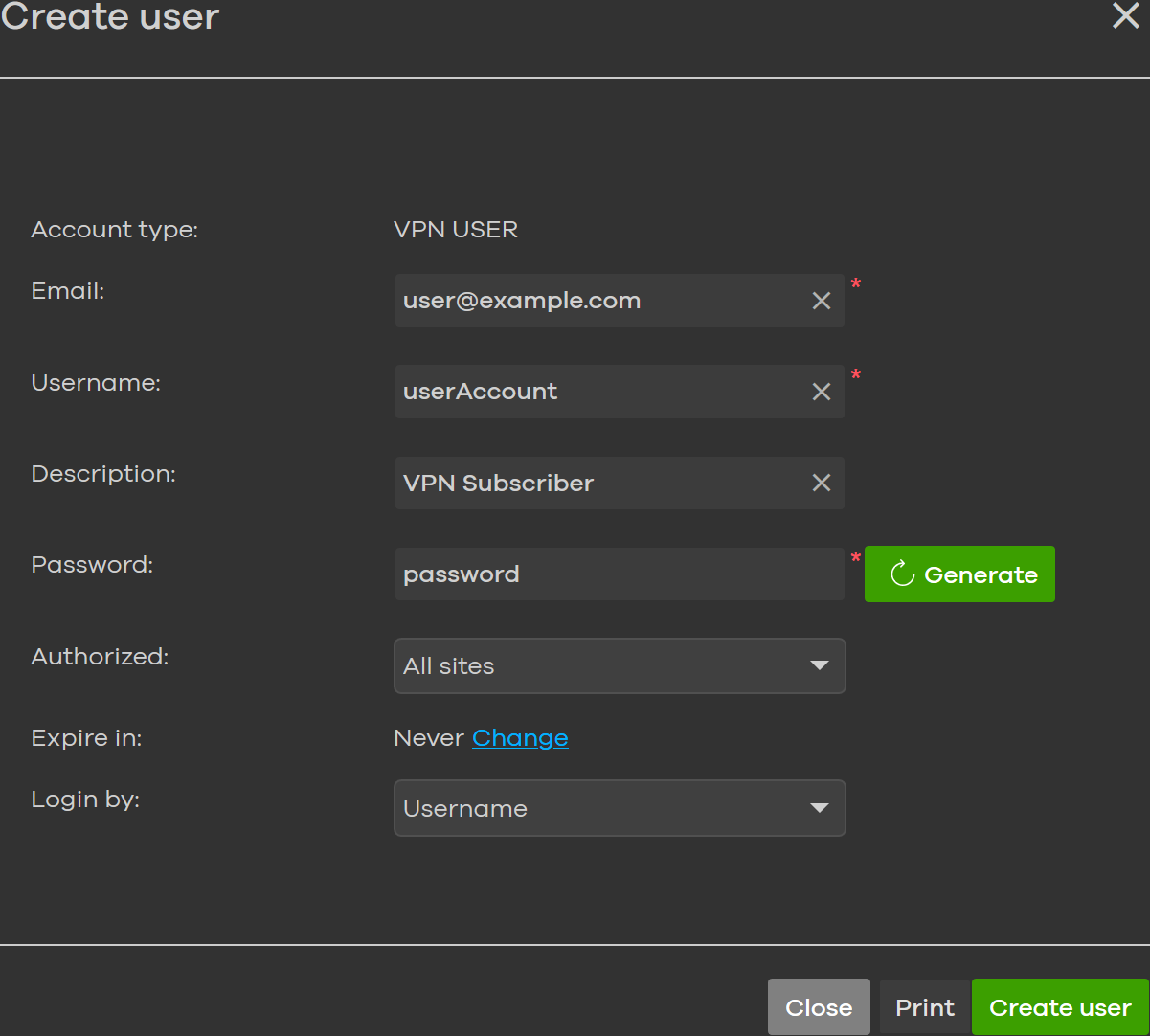
Create a VPN client account in Organization-wide → Configure → Cloud authentication if your auth. type is Nebula Cloud Authentication.
IPSecuritas VPN Client Setup
The IPSecuritas VPN Client is a free VPN application for macOS computers. You can download a copy of the client from here. Because the client is not manufactured or engineered by Zyxel we do not offer technical support for the client. Any issues related to the software need to be brought to the attentions of Lobotomo Software.
To configure the VPN client based on the NebuilaCC setup example above, please open the program which is located in your Mac's Applications folder. On the applications toolbar click on the "Connections" menu and select "Edit Connections". On the connection editor window click on the "+" sign to add a VPN policy.
On the clients "General" tab make the following changes to the setup:
- Remote IPSec Device – Type in the domain name/DDNS hostname or public IP address of the VPN gateway.
- Local Side – Set the "Endpoint Mode" to Auto.
- Remote Side – Set the "Endpoint Mode" to Network and enter in the NebulaCC address subnet you wish to access.
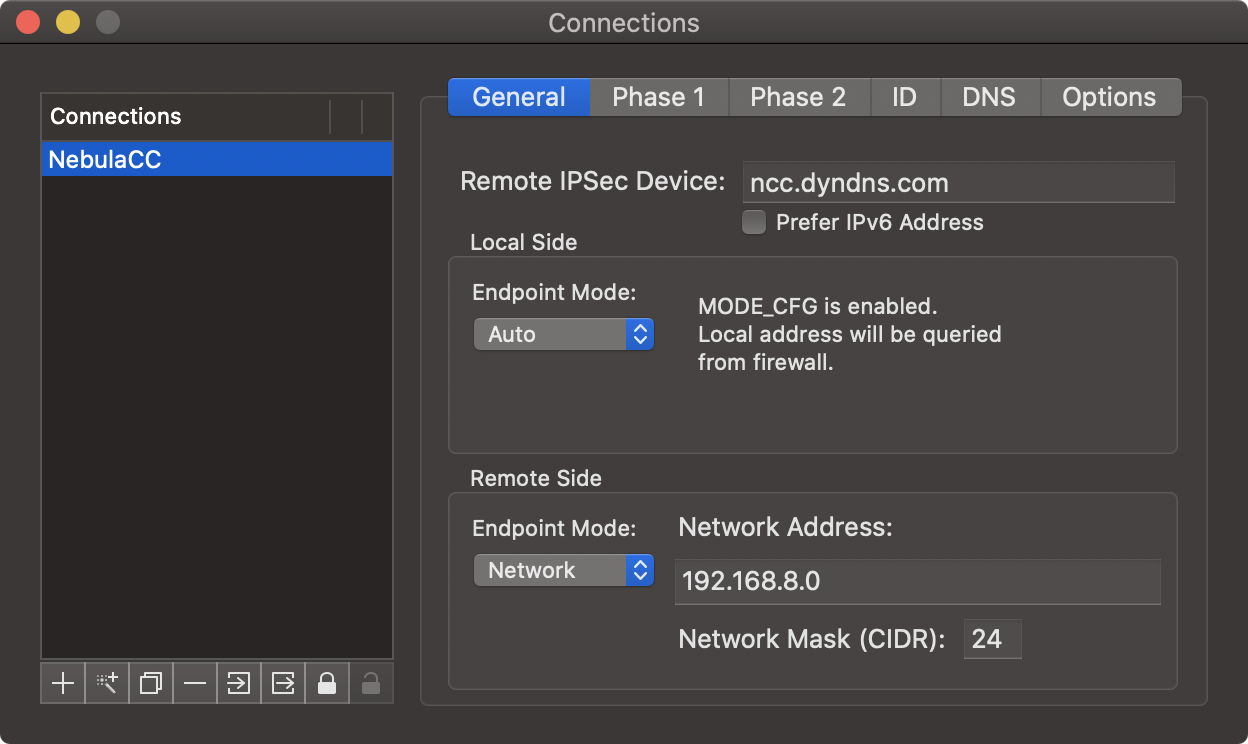
Click the "Phase 1" tab and make the following changes to the setup:
- Lifetime – The lifetime is the amount of time, in seconds, before the client re-negotiates the algorithms.
- DH Group – Set this to 1024 (2), also known as DH2.
- Encryption – Set this to 3DES.
- Authentication – Set this to SHA-1.
- Exchange Mode – Set this to Main.
- Proposal Check – Leave the option as it is (Obey by default)
- Nonce Size – Leave the option as it is (16 by default)
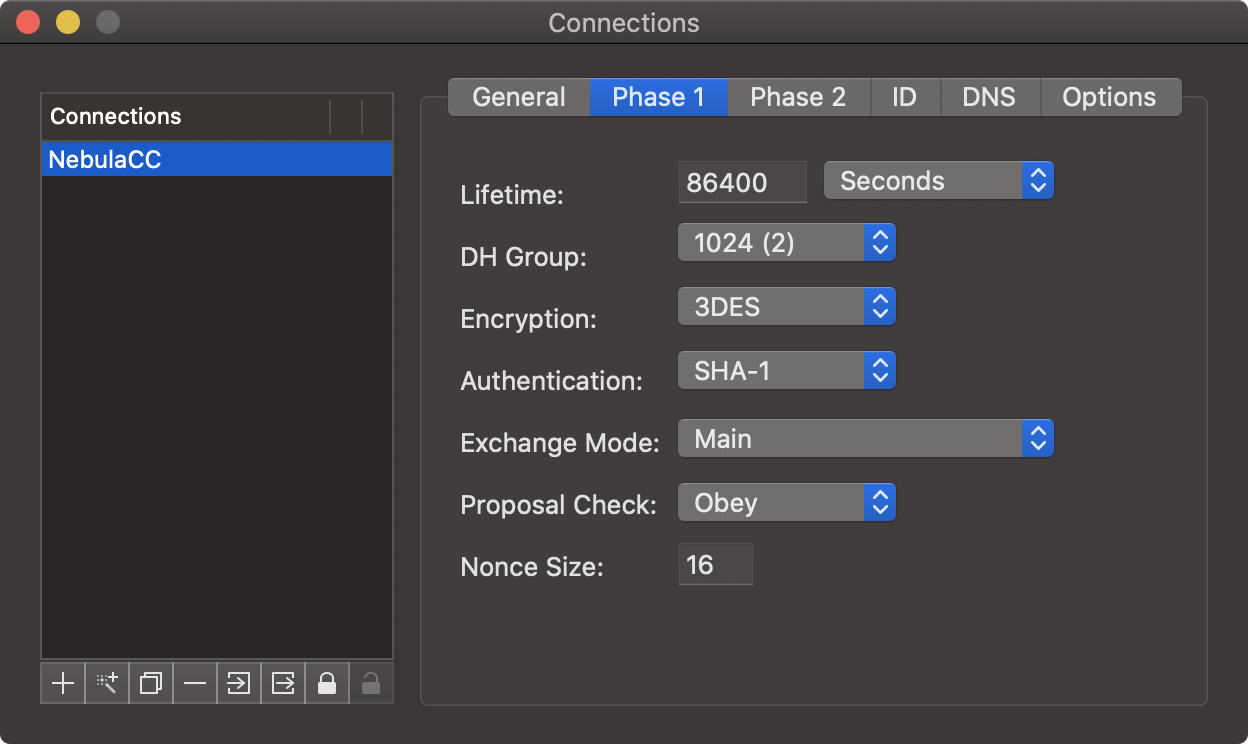
Click the "Phase 2" tab and make the following changes to the setup:
- Lifetime – The lifetime is the amount of time, in seconds, before the client re-renegotiates the algorithms.
- PFS Group – Set this to None.
- Encryption – Set this to 3DES.
- Authentication – Set this to SHA-1.
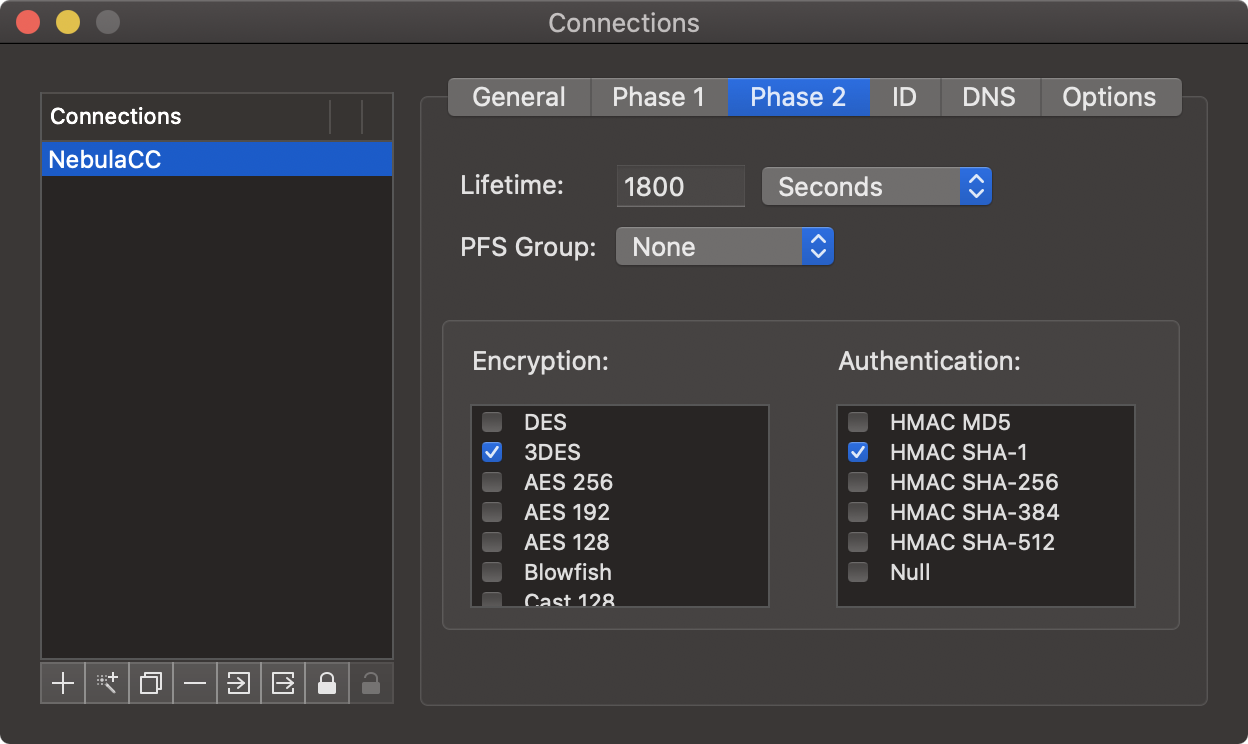
Click the "ID" tab and make the following changes to the setup:
- Local Identifier – Leave the option as is (Address by default).
- Remote Identifier – Leave the option as is (Address by default).
- Authentication Method – Set this option to use XAuth PSK.
- Preshared Key – Type in the same key created for the Nebula CC VPN connection.
- Username – Provide the VPN user account name you created on the Nebula CC.
- Store Password – Check the box to enter account password and save the setting to the IPSecuritas VPN profile. Leave this unchecked if you wish to be asked for the user password upon connection.
Click the "DNS" tab and make the following changes to the setup:
- No changes need to be made here. DNS server entries should only be added if web traffic will flow through the VPN tunnel as well. If the VPN is only used to access network resources on the other end, DNS is not needed.
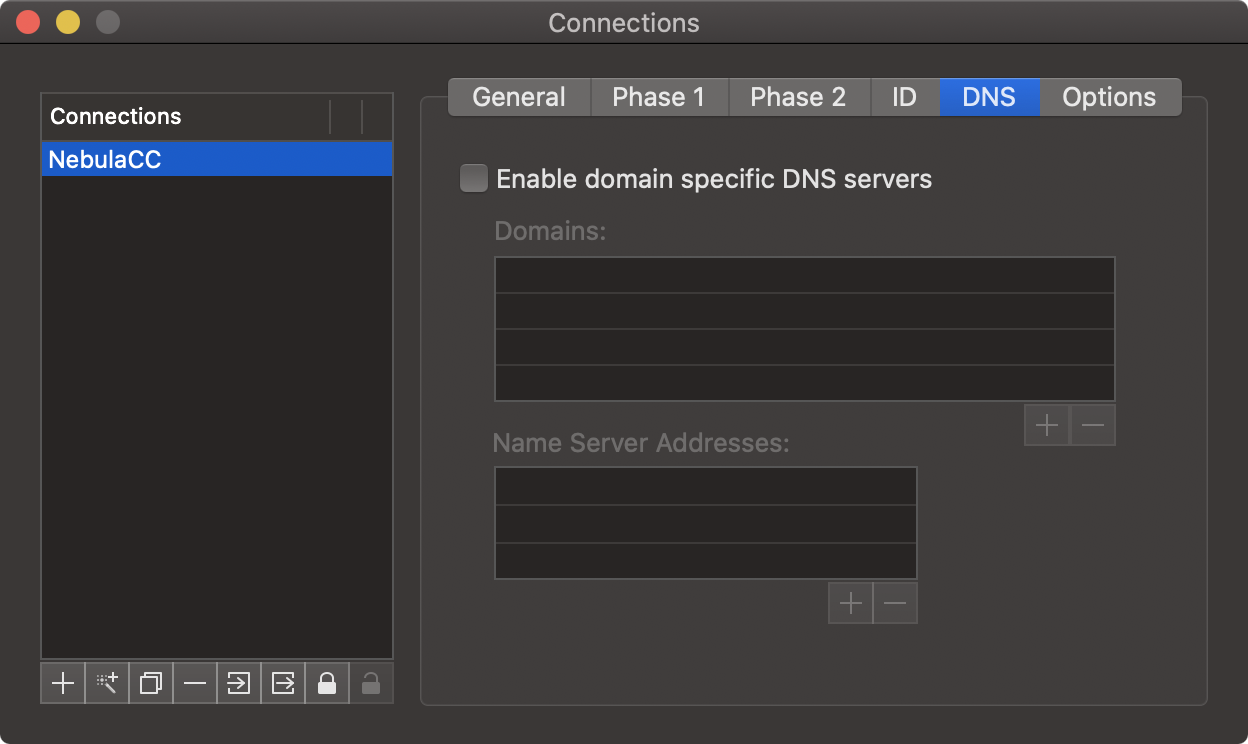
Click the "Options" tab and make the following changes to the setup:
- IPSec DOI – This option should be checked.
- SIT_IDENTITY_ONLY – This option should be checked.
- Verify Identifier – This option should be unchecked.
- Initial Contact – This option should be checked.
- Local IP in Remote Network – This option should be unchecked.
- Disable collision check – This option should be unchecked.
- Support Proxy – This option should be unchecked.
- Request Certificate – This option should be unchecked.
- Verify Certificate – This option should be unchecked, we are using Pre-Shared Keys instead of certificate authentication.
- Send Certificate – This option should be unchecked.
- Unique SAs – This option should be unchecked.
- IKE Fragmentation – This option should be unchecked.
- NAT-T – This option is disabled. NAT-T should only be used if the VPN router is behind a NAT with no VPN passthrough support.
- Enable Connection Check – This option allows the client to send an ICMP/PING packet to test the connection. If the option is enabled a reliable host should be used to run the ICMP/PING test, otherwise the connection may be unstable.
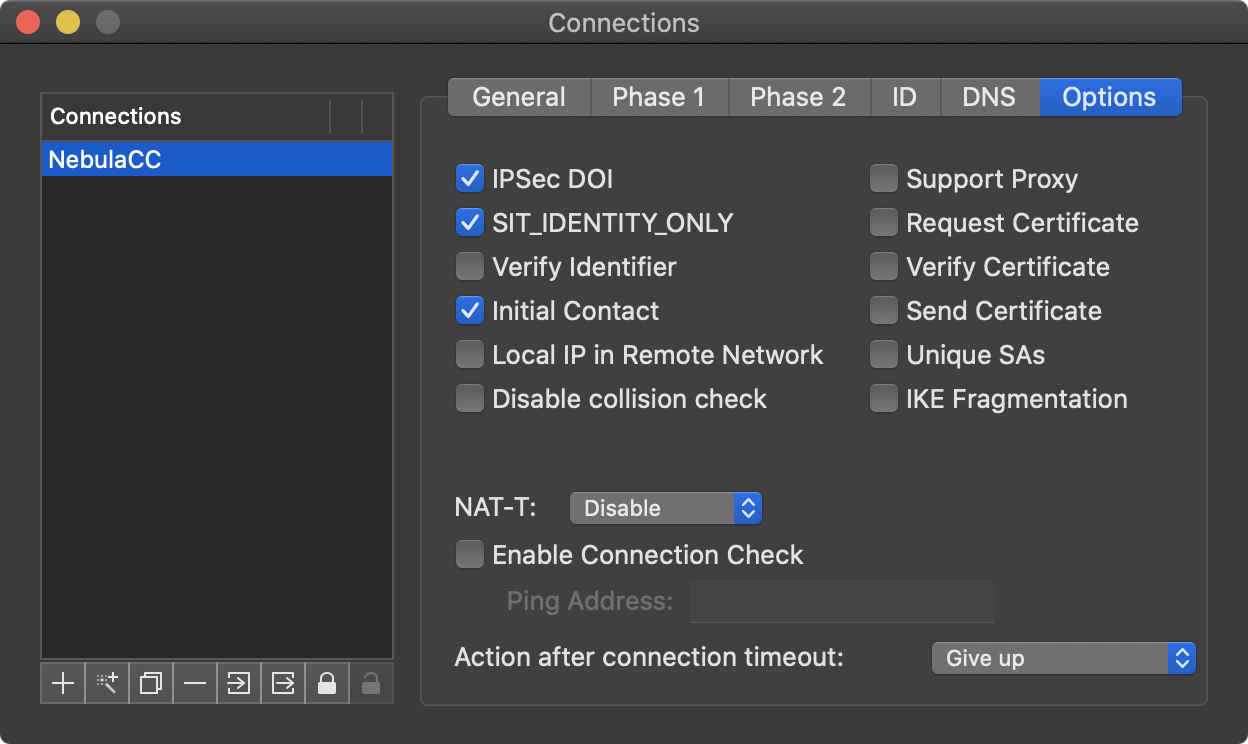
Now that the VPN policy has been created on the IPSecuritas software you can dial the VPN connection by selecting the rule you wish to connect and pressing the "Start" button. This will begin the VPN connection process.
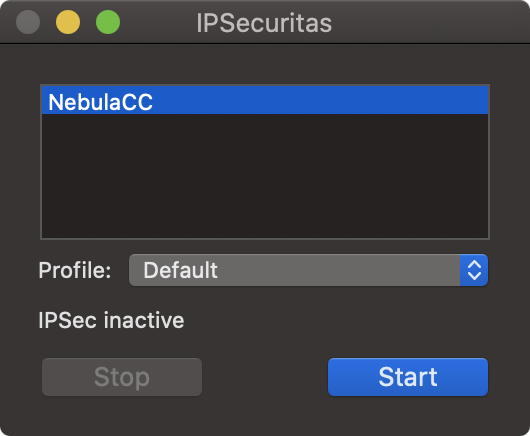
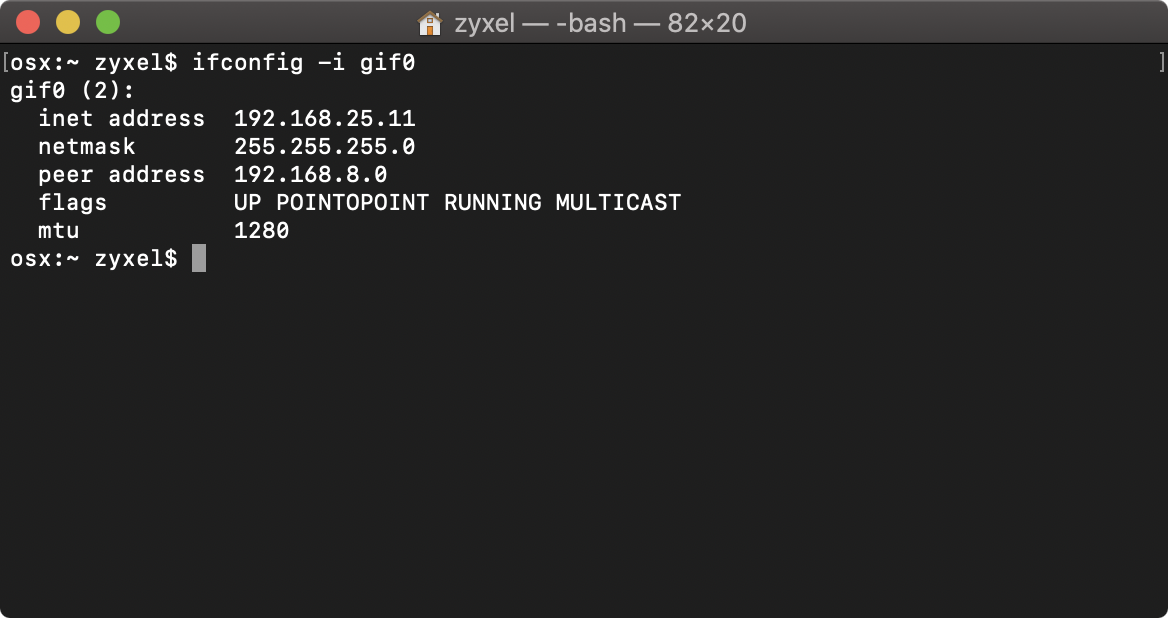
Once the tunnel is established open a terminal window and attempt to ping a device across the VPN tunnel to verify traffic is passing through.
Note: Make sure the device you are pinging is set to respond to ICMP/PING requests.
You can also run the ifconfig command to verify that you are getting an IP address for the tunnel adapter and that it is within the range configured on NebulaCC.
Comments
0 comments
Please sign in to leave a comment.