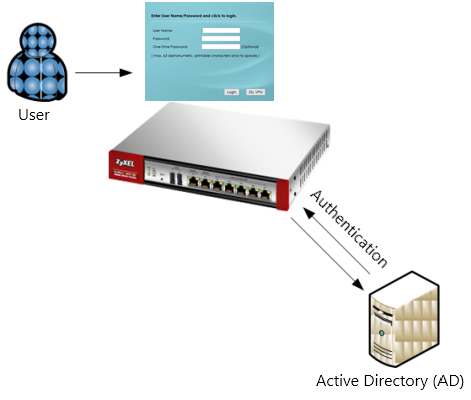
Scenario
Users which login to SSL VPN or normal authentication can be authenticated through an Active Directory, LDAP or RADIUS server.
This guideline shows how to setup the communication between ZyWALL/USG and Active Directory server.
Supported Devices
ZyWALL 110
ZyWALL 310
ZyWALL 1100
USG40
USG40W
USG60
USG60W
USG110
USG210
USG310
USG1100
USG1900
USG20-VPN
USG20W-VPN
USG2200-VPN
Create Active Directory
To create a connection between the ZyWALL/USG and an Active Directory, we need to configure the settings as an AAA Server object.
Go to the Configuration(![]() ) → Object → AAA Server menu, select the already created "AD" profile and click Edit.
) → Object → AAA Server menu, select the already created "AD" profile and click Edit.
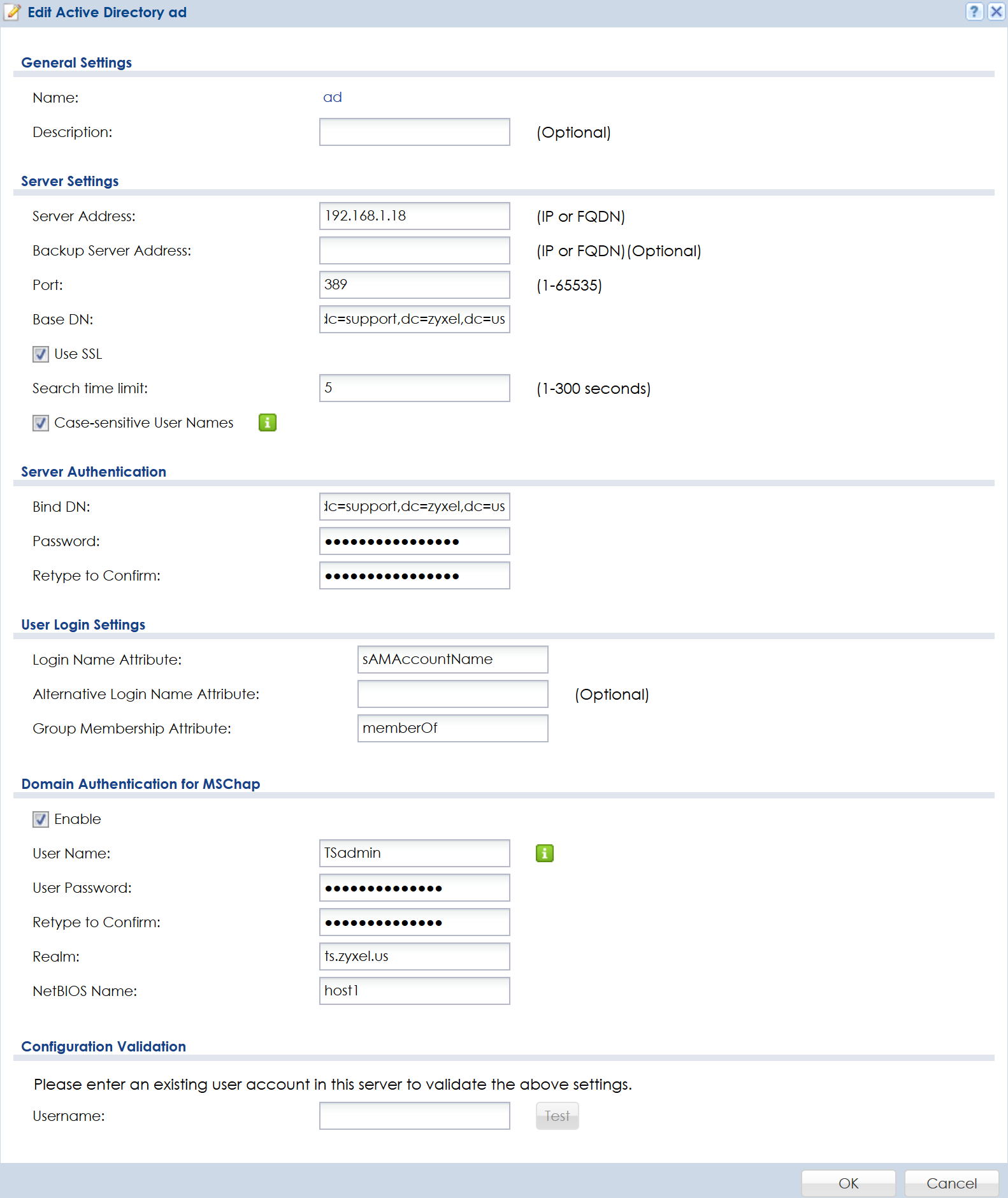
- Type a description. [optional]
- Insert your AD-server's IP-address.
- Insert the backup AD server address. [if any]
- Set the AD port. [if different]
- Base DN: dc=support,dc=zyxel,dc=us (for the domain support.zyxel.us)
- Check the box to Use SSL. [if secure connection enabled in AD]
- Check "Case-sensitive User Names". [if applicable]
- Bind DN: cn=Administrator,cn=Users,dc=support,dc=zyxel,dc=us (for the Administrator account in Users folder)
- Type the password for the Administrator account.
- Domain Authentication for MSCHAP (enable and configure if used by AD)
For items that are stored in an Organizational Unit, use "ou" instead of "cn".
Note: You can test a user in the Configuration Validation field.
Active Directory to Authentication Method
To make the ZyWALL/USG look in the Active Directory, we need to select our AD in the Authentication Method settings. Go to the Configuration(![]() ) → Object → Auth. Method menu. Edit the default rule.
) → Object → Auth. Method menu. Edit the default rule.
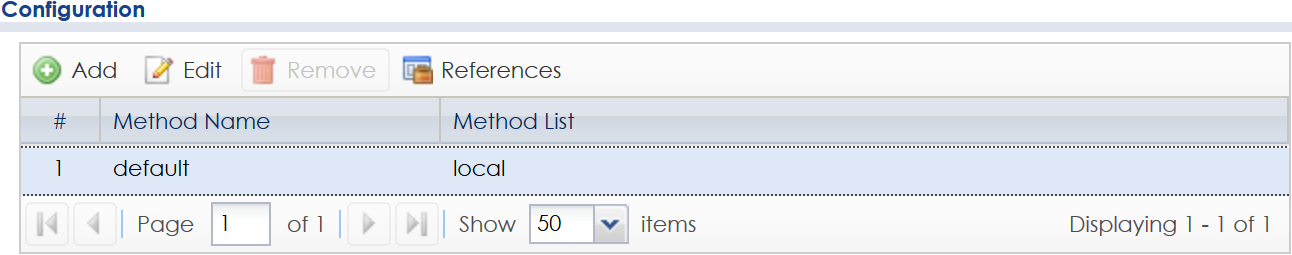
Click the Add button, and select "group ad".
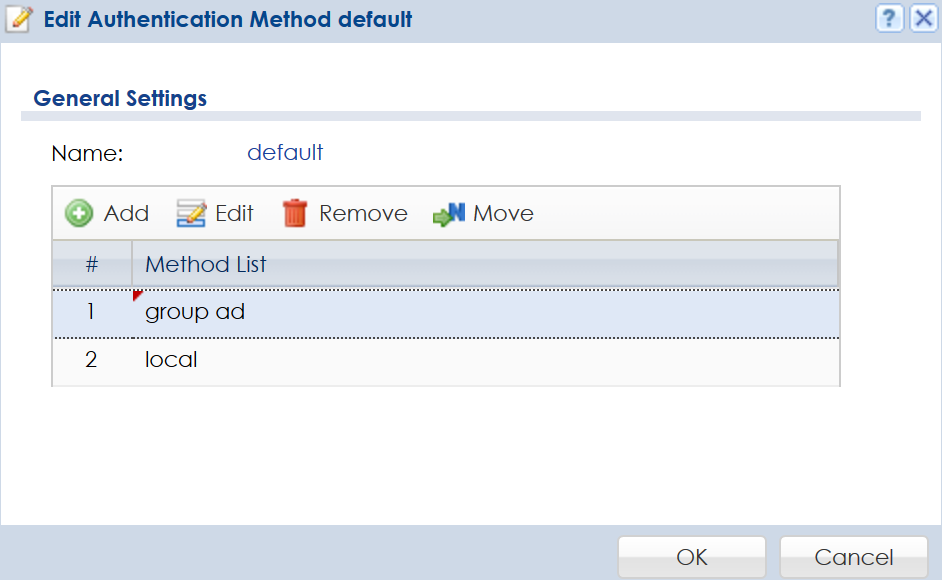
If after adding the "group ad" it is not in first place, click to highlight the object and click Move. Type "1", and press Enter on your keyboard to move the item to the first position.
Once "group ad" is in the first position, click OK.
Now the ZyWALL/USG will ask the Active Directory, before it checks its local database.
Comments
0 comments
Please sign in to leave a comment.