Scenario
Out of the box the LAN1 and LAN2 networks have no restrictions as to what interface they can communicate with. LAN1 and LAN2 have access to communicate with the DMZ, WAN and any VLAN interface created in the Zyxel device. Some networks may not like this, as they may use LAN2 as a guest network, for example. The LAN2 having unrestricted access over all interfaces would not be good practice in this type of scenario. Below are instructions on what changes need to be made to lock down the networks better.
Supported Devices
ZyWALL 110
ZyWALL 310
ZyWALL 1100
USG40
USG40W
USG60
USG60W
USG110
USG210
USG310
USG1100
USG1900
USG20-VPN
USG20W-VPN
USG2200-VPN
Edit Policy Control Rules
To keep the LAN1, LAN2, etc., from communicating with each other, please go to menu Configuration(![]() )→Security Policy→Policy Control. The top 2 rules are for LAN1 and LAN2 to ANY traffic (LAN*_Outgoing). These rules allow both networks to communicate with the Internet, DMZ, VLAN's, etc. To change this, edit each rule and change the "To:" option to WAN instead of ANY. This change will allow the LAN to communicate with the internet and not an internal interface.
)→Security Policy→Policy Control. The top 2 rules are for LAN1 and LAN2 to ANY traffic (LAN*_Outgoing). These rules allow both networks to communicate with the Internet, DMZ, VLAN's, etc. To change this, edit each rule and change the "To:" option to WAN instead of ANY. This change will allow the LAN to communicate with the internet and not an internal interface.
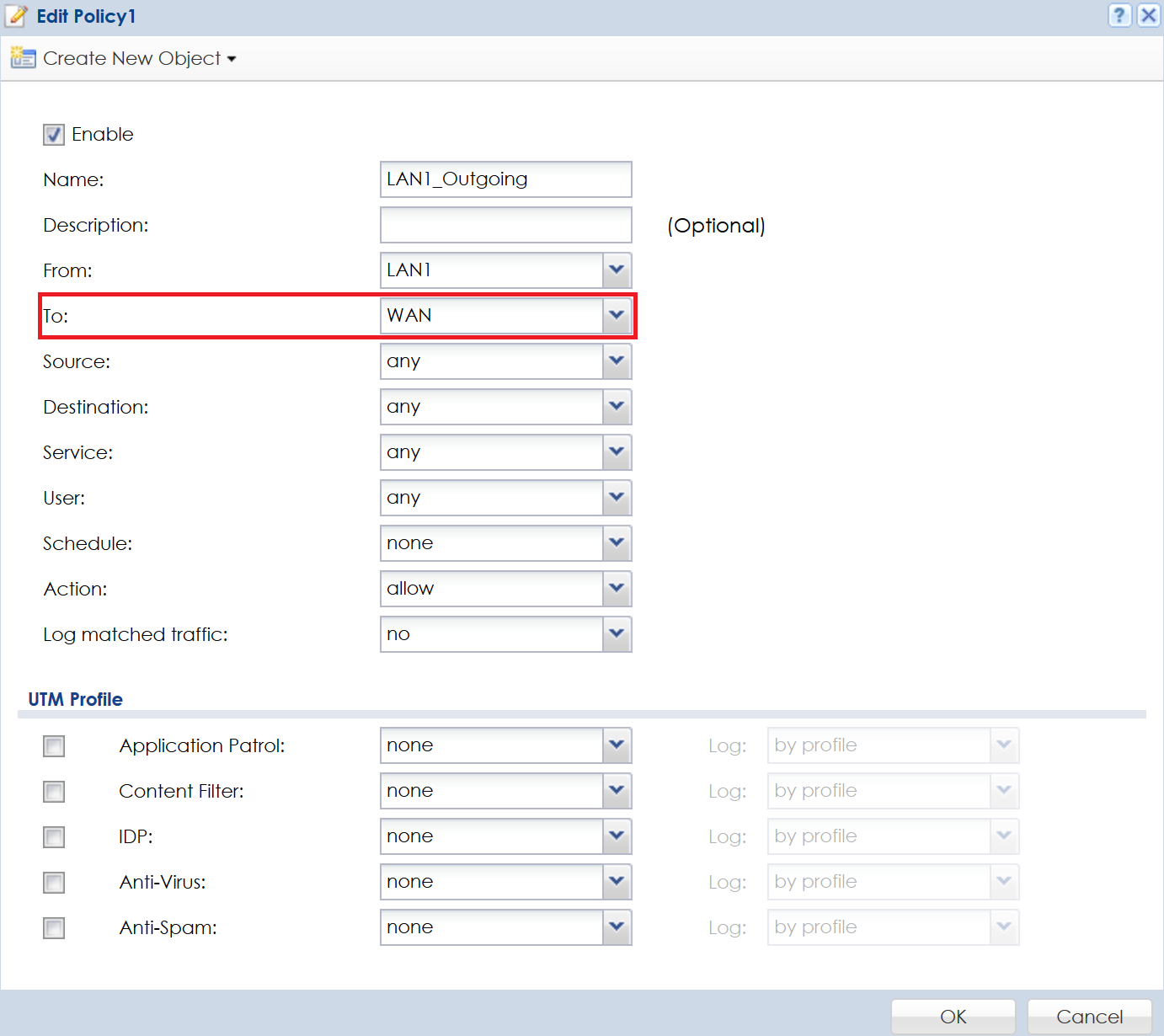
Click the OK button to save the settings and repeat the process for the other "LAN*_Outgoing" rule.
Comments
0 comments
Please sign in to leave a comment.