This guide provides an example on creating an IPSec VPN rule between two sites using ISP DHCP (dynamic IP's).
Overview
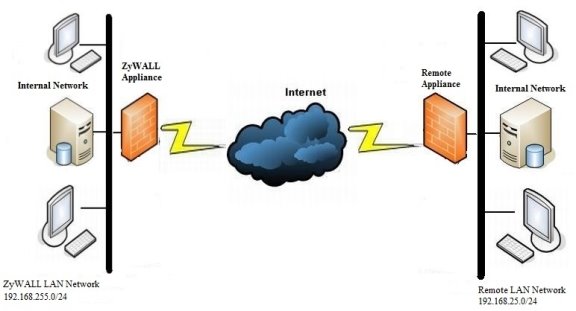
A VPN (Virtual Private Network) provides a secure communication between sites without the expense of leased lines. VPNs are used to transport traffic over the Internet of any insecure network that uses TCP/IP communications. A Site-to-Site VPN (router-to-router) allows multiple sites to network their resources together into one network.
Scenario:
Both sites have dynamic IP addresses on the public side (internet). To be able to establish a VPN connection between the two sites it is recommended that DDNS be configured. Because the internet connection is dynamic, the public IP can change at any time, this will break the VPN connection and require further input from the user to re-establish the link. Using DDNS will provide the ability to re-establish the VPN connection without input from the user.
Supported Devices
ZyWALL 110
ZyWALL 310
ZyWALL 1100
USG40
USG40W
USG60
USG60W
USG110
USG210
USG310
USG1100
USG1900
USG20-VPN
USG20W-VPN
USG2200-VPN
Table of Content
Network Address Object
VPN Gateway (Phase 1)
VPN Connection (Phase 2)
Remote router VPN Gateway
Remote router VPN Connection
Troubleshooting
Accessing the WebUI
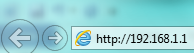
To access the ZyWALL web configuration page please open a web browser on your computer (Internet Explorer, Mozilla Firefox, Google Chrome, etc.). On the address bar type, http://192.168.1.1 and press ENTER/RETURN to access the WebUI.
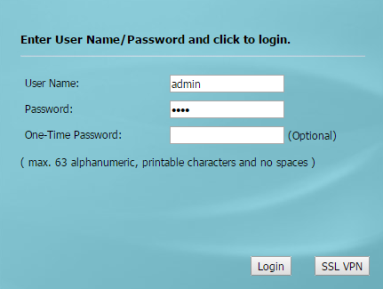
When prompted for user credentials, type in admin for the "User Name" and 1234 for the "Password". Click the LOGIN button to enter the WebUI.
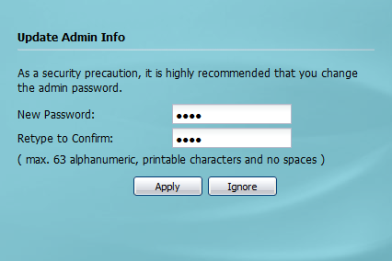
The following screen will prompt to update the administrator password. Enter a new administrative password and click the "Apply" button to save the change.
Click "Ignore" to keep the default password (1234) and continue with the setup.
Network Address Object
From the WebUI go to menu, Configuration → Object → Address. Click the Add button on the menu to add an entry. This must be done on both VPN routers. The address entry will reflect the remote network LAN IP scheme (the IP network that will be allowed communications over the tunnel).
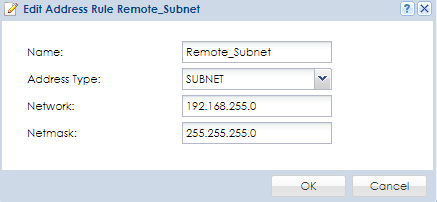
- Provide a name for the address object entry
- Specify what "Address Type" this object is for [HOST (single IP address, SUBNET (network IP scheme, RANGE (range of IP addresses)]
- Type in the IP criteria based on the address type selected
- Press OK to save/apply the settings.
Object created in ZyWALL Appliance:
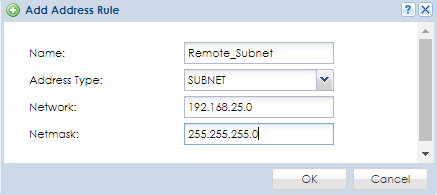
Object created in Remote Appliance:
VPN Gateway (Phase 1)
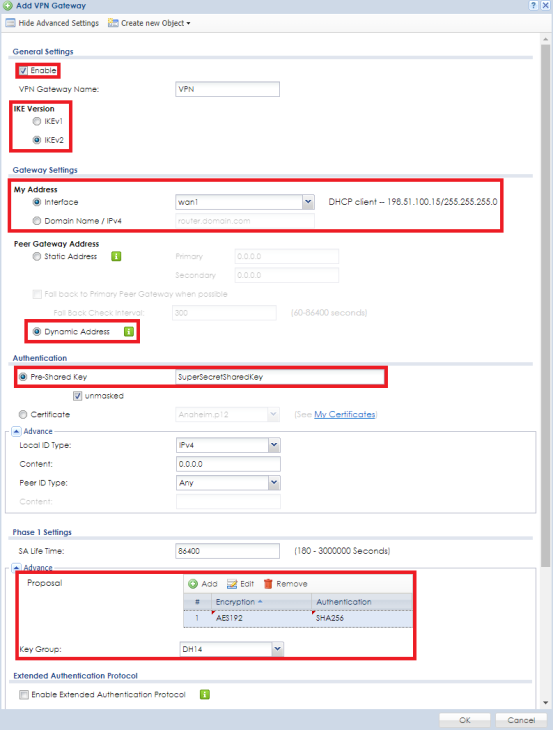
To create the VPN rule (policy) go to menu, Configuration → VPN → IPSec VPN. In the IPSec VPN menu click the "VPN Gateway" tab to add Phase 1 of the tunnel setup. Click the Add button to insert a new rule. On the top left of the window click the "Show Advance Settings" button to view all available setup options in the menu.
- Check the box to enable the VPN rule and provide a name.
- Select IKE Version to use: IKEv1/IKEv2.
- Select the WAN interface you wish to use to connect the VPN under the My Address dropdown field, or, select "Domain Name/IPv4" to manually type in the public IP address or domain/DDNS hostname.
- For "Peer Gateway Address" select the Dynamic Address option.
- Under Authentication create a "Pre-Shared Key".
- Under the Phase 1 Settings select the desired security algorithms.
- Set the "Encryption" and "Authentication" proposal you wish to use (Encryption options are DES, 3DES, AES128, AES192, AES256) (Authentication options are MD5, SHA1, SHA256, SHA512) Settings must match both sites
- Select the Diffie-Hellman key group (options are DH1, DH2, DH5) Settings must match both sites
- Click the OK button to save/apply the settings
Note: The caution symbol to the right will appear on areas where input is required or if there is a mistake with the entry, such as illegal/unsupported characters.
VPN Connection (Phase 2)
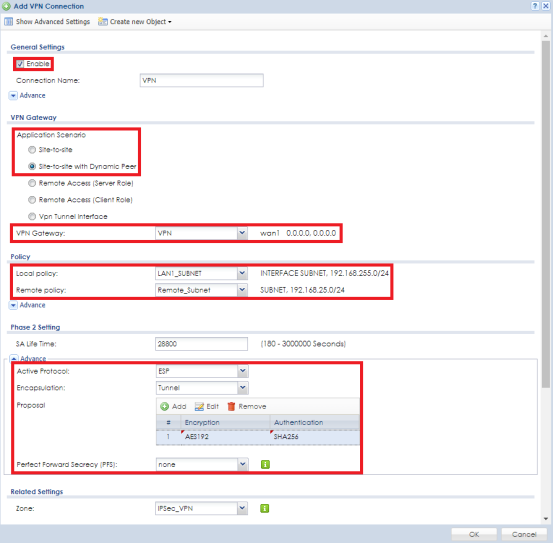
Now that the VPN Gateway (Phase1) rule has been created click on the "VPN Connection" tab to insert the Phase 2 rule for the VPN tunnel. Click the Add button to insert a new rule entry. On the top left of the window click the "Show Advance Settings" button to view all available setup options in the menu.
- Check the box to enable the rule and give it a name
- Enable Nailed-Up ( this option needs to be enabled on one of the routers only, this is the VPN keep alive option, whichever site has this enabled will dial the connection, the site with this option disabled will listen for the connection)
- Set the VPN Gateway application scenario to use "Site-to-Site with Dynamic Peer"
- On the application scenario set the VPN Gateway dropdown to use the Phase 1 policy that was created on the previous step. (VPN for this example)
- Scroll down to the Policy option and set the Local Policy to use the "LAN1_SUBNET" address object, this will give the VPN user access over all devices connected to LAN1
- For Remote Policy click the dropdown and select the remote networks IP object (Remote_Subnet for this example)
- Active Protocol under the Phase 2 Setting should be set to "ESP"
- The Encapsulation is "Tunnel"
- Set the "Encryption" and "Authentication" proposal you wish to use (Encryption options are DES, 3DES, AES128, AES192, AES256) (Authentication options are MD5, SHA1, SHA256, SHA512) Settings must match both sites
- Perfect Forward Secrecy (PFS) is an added level of encryption, it is not necessary to enable it, but, if you wish to use the added encryption level the options are None, DH1, DH2 and/or DH5 Settings must match both sites
- Under Related Settings make sure the Zone is set for "IPSec_VPN"
- Click the OK button to save/apply the settings
Note: The caution symbol to the right will appear on areas where input is required or if there is a mistake with the entry, such as illegal/unsupported characters.
Now that Phase 1 and Phase 2 of the VPN rule have been completed, uncheck the box to "Use Policy Route to control dynamic IPSec rules". Unchecking this option will allow the ZyWALL to automatically create routes for connected VPN users. Click the Apply button at the bottom of the window to save the changes.
Remote router VPN Gateway
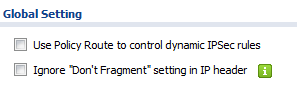
To create the VPN rule (policy) go to menu Configuration → VPN → IPSec VPN. In the IPSec VPN menu click the "VPN Gateway" tab to add Phase 1 of the tunnel setup. Click the Add button to insert a new rule. On the top left of the window click the "Show Advance Settings" button to view all available setup options in the menu.
- Check the box to enable the VPN rule and provide a name
- Select IKE Version: IKEv1/IKEv2 (this must match selection on Step B)
- Select the WAN interface you wish to use to connect the VPN under the My Address dropdown field or select "Domain Name/IPv4" to manually type in the public IP address or domain/DDNS hostname.
- For "Peer Gateway Address" select the Static Address option and type in the remote router's public IP address or domain/DDNS hostname.
- Under Authentication type the "Pre-Shared Key" created on Step B.
- Under the Phase 1 Settings select the desired security algorithms.
- Set the "Encryption" and "Authentication" proposal you wish to use (Encryption options are DES, 3DES, AES128, AES192, AES256) (Authentication options are MD5, SHA1, SHA256, SHA512) Settings must match both sites
- Select the Diffie-Hellman key group (options are DH1, DH2, DH5) Settings must match both sites
- Click the OK button to save/apply the settings
Note: The caution symbol to the right will appear on areas where input is required or if there is a mistake with the entry, such as illegal/unsupported characters.
Remote router VPN Connection
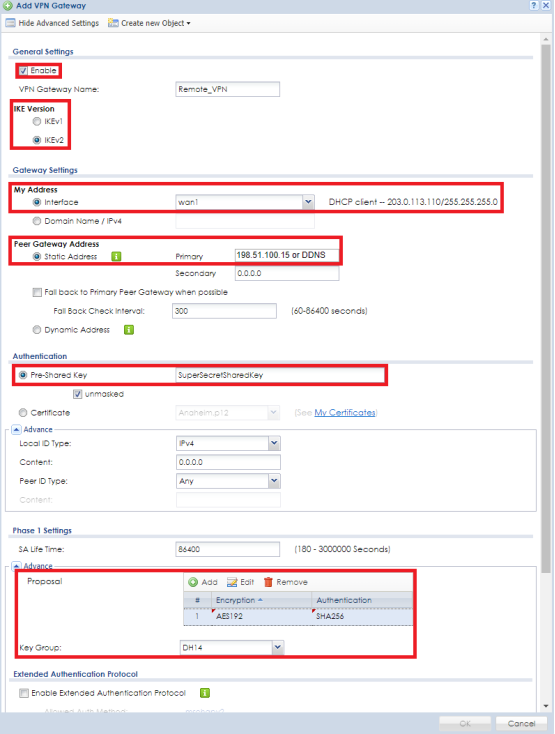
Now that the VPN Gateway (Phase1) rule has been created click on the "VPN Connection" tab to insert the Phase 2 rule for the VPN tunnel. Click the Add button to insert a new rule entry. On the top left of the window click the "Show Advance Settings" button to view all available setup options in the menu.
- Check the box to enable the rule and give it a name
- Enable Nailed-Up (this is the VPN keep alive option)
- Set the VPN Gateway application scenario to use "Site-to-Site"
- On the application scenario set the VPN Gateway dropdown to use the Phase 1 policy that was created on the previous step. (Remote_VPN for this example)
- Scroll down to the Policy option and set the Local Policy to use the "LAN1_SUBNET" address object, this will give the VPN user access over all devices connected to LAN1
- For Remote Policy click the dropdown and select the remote networks IP object (Remote_Subnet for this example)
- Active Protocol under the Phase 2 Setting should be set to "ESP"
- The Encapsulation is "Tunnel"
- Set the "Encryption" and "Authentication" proposal you wish to use (Encryption options are DES, 3DES, AES128, AES192, AES256) (Authentication options are MD5, SHA1, SHA256, SHA512) Settings must match both sites
- Perfect Forward Secrecy (PFS) is an added level of encryption, it is not necessary to enable it, but, if you wish to use the added encryption level the options are None, DH1, DH2 and/or DH5 Settings must match both sites
- Under Related Settings make sure the Zone is set for "IPSec_VPN"
- Click the OK button to save/apply the settings
Note: The caution symbol to the right will appear on areas where input is required or if there is a mistake with the entry, such as illegal/unsupported characters.
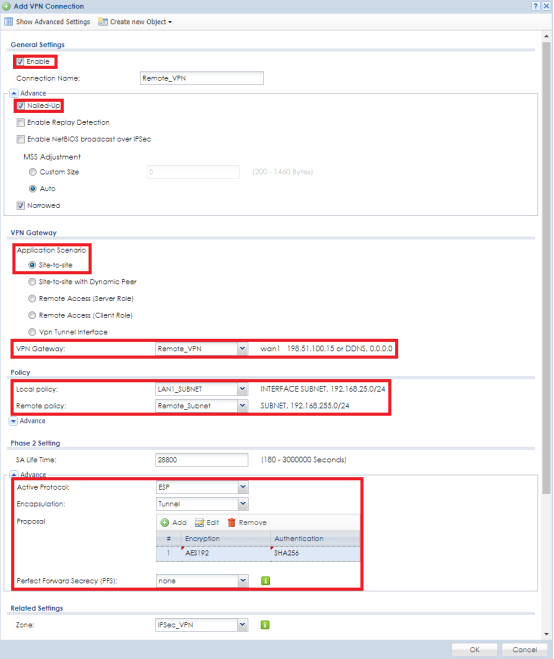
Now that Phase 1 and Phase 2 of the VPN rule have been completed, uncheck the box to "Use Policy Route to control dynamic IPSec rules". Unchecking this option will allow the ZyWALL to automatically create routes for connected VPN users. Click the Apply button at the bottom of the window to save the changes.

Troubleshooting
VPN will not establish
If you have configured an IPSec VPN rule for site-to-site (router-to-router) connection and the tunnel is not being established, please try the following:
- Reboot/Restart the ZyWALL appliance to reload the VPN daemon.
- Check the ZyWALL logs to verify that IKE connection attempts are being sent and received. If the logs show one way IKE traffic, send only for example, check the internet connection to make sure traffic is not being blocked/stopped on the service end.
- Double check the VPN rules on both ends to make sure all settings are matching.
- If using DDNS hostname or domain name to dial the connection instead of the public IP address, please make sure there are DNS servers programmed on the ZyWALL and that they can resolve the DDNS hostname/domain name. To check if the ZyWALL can resolve the name you will need to open a terminal session using SSH/Telnet/Console and run a ping command to the DDNS hostname/domain name.
Router> ping hostname/domain (ex: Router> ping www.google.com)
If the ping test fails double check the ZyWALL DNS settings and try again. If your internet service is DHCP the ZyWALL would have automatically obtained the DNS server settings from your ISP. To check this go to Configuration → System → DNS.
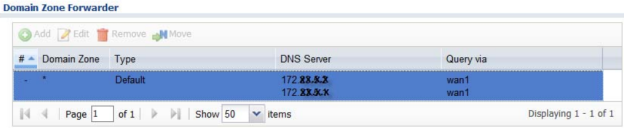
If your WAN IP was statically assigned the DNS settings will show "N/A" for the Default entry (the Default entry is for the WAN ports DHCP client capability only), click the Add button to manually enter your ISP provided or public (OpenDNS, Google DNS, etc.) DNS servers.
- Verify the firmware is up to date and contact tech support for further assistance. To check the current version of firmware on the ZyWALL go to Maintenance → File Manager → Firmware Package
No traffic flow through site-to-site IPSec VPN tunnel
Tunnel established but can't get traffic across:
- Make sure there are no IP conflicts between the two sites.
- Disable the ZyWALL routers firewall.
To disable the ZyWALL firewall/policy control, go to:
Configuration → Firewall OR Configuration → Security Policy → Policy Control 
- Verify that the host you are attempting to reach is pointing to the ZyWALL for the default gateway.
- Verify that the host you are attempting to reach is listening for the traffic you are sending to it. Example: If you're sending a ping request to a device, make sure it is set to respond to ping/icmp requests.
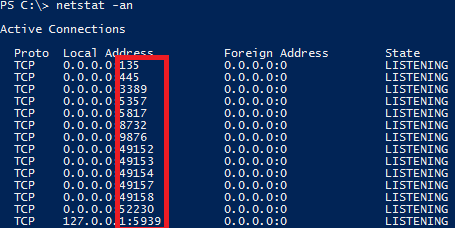
Windows: Open command prompt or PowerShell and type 'netstat -an' for a list of listening ports.
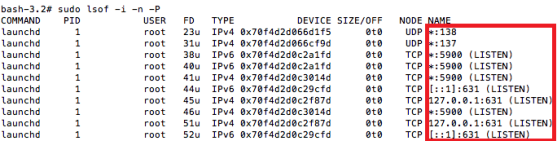
Linux/Mac OS X: Open terminal and type sudo lsof -i -n -P for a printout of the listening ports.
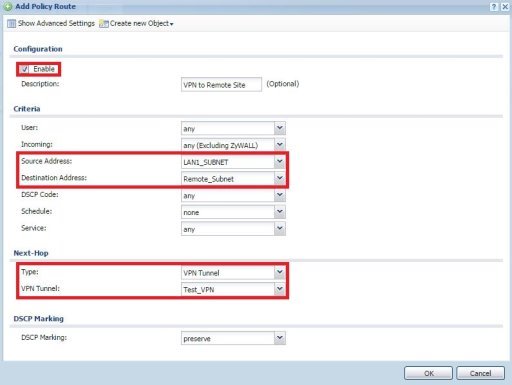
- Manually create a route (Configuration → Routing) to stipulate that traffic destined for the remote network should take its Next-Hop on the appropriate VPN tunnel.
Comments
0 comments
Please sign in to leave a comment.