This walkthrough will cover how to isolate/segregate/separate internal LAN traffic, to prevent from spilling into other internal networks (LAN1, LAN2, DMZ, etc.).
Supported Devices
ZyWALL 110
ZyWALL 310
ZyWALL 1100
USG40
USG40W
USG60
USG60W
USG110
USG210
USG310
USG1100
USG1900
USG20-VPN
USG20W-VPN
USG2200-VPN
Isolating Interfaces
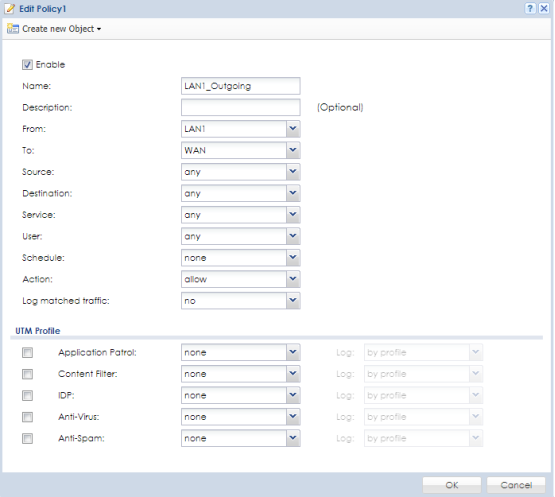
To configure the ZLD appliance to isolate traffic between interfaces please access the device WebUI. Go to menu, Configuration → Security Policy → Policy Control. Edit the rules for the interfaces you wish to isolate. For instance, the "LAN1_Outgoing" rule allows the LAN1 interface to communicate with ANY other interface (this includes the WAN, LAN2 and DMZ). Editing this rule to read from LAN1 to WAN, instead or ANY, will allow the LAN1 to communicate only with the WAN interface for internet access. From this point on LAN1 communications with LAN2 or DMZ will cease.
Comments
0 comments
Please sign in to leave a comment.