This example illustrates how to create a FQDN object and configure a security policy rule to allow remote clients at home which have dynamic IP address to connect to HQ's ZyWALL firewall via SSH.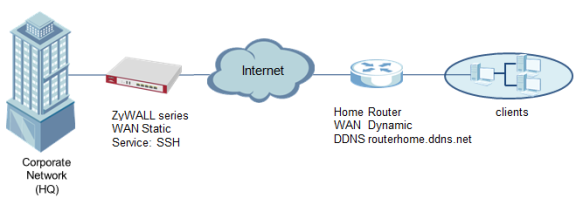
Figure 1 Allow Remote Management from DDNS Clients Note: All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses. This example was tested using the VPN100 (Firmware Version: ZLD 4.30).
Note: All network IP addresses and subnet masks are used as examples in this article. Please replace them with your actual network IP addresses. This example was tested using the VPN100 (Firmware Version: ZLD 4.30).
Create a FQDN Object
In the ZyWALL firewall, go to CONFIGURATION > Object > Address/Geo IP > Address > Add to create a FQDN object home. Select the FQDN as the address type and fill in the domain name of the remote clients.
CONFIGURATION > Object> Address/Geo IP > Address > Add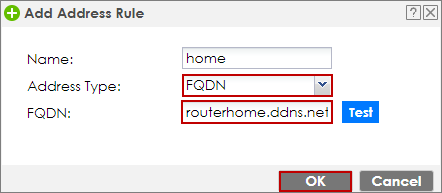
Set Up the Security Policy for Remote Clients
In the ZyWALL firewall, go to CONFIGURATION > Security Policy > Policy Control > Policy > Add, configure a Name for you to identify the Security Policy Profile. Allow SSH traffic from the WAN zone to the ZyWALL from the source address home. Select log to monitor the result.
CONFIGURATION > Security Policy > Policy Control > Policy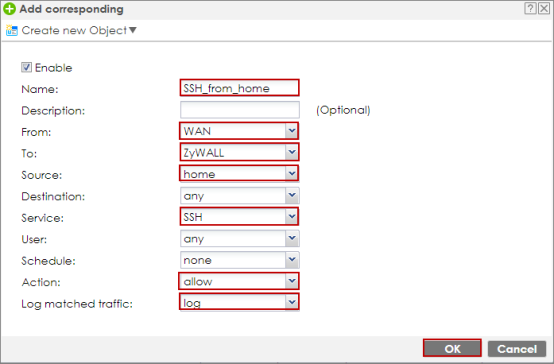
Test the Result
- Go to MONITOR > System Status > FQDN Object to check FQDN object cache list.
MONITOR > System Status > FQDN Object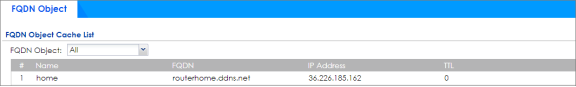
- On the PC of the remote client, connect via SSH to ZyWALL firewall. Go to MONITOR > Log. You can see that the remote client is allowed to access from WAN via SSH even if its IP address is dynamic.
MONITOR > Log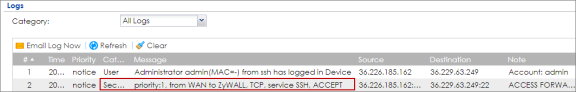
What Can Go Wrong?
- FQDN objects cannot be in an address group with other address types. Do not mix FQDN object with other address object types in the same object group. You can create an address group object and all members in it must be FQDN address type.
- Wildcard is supported in the FQDN pattern, for example: *.google.com, but wildcard FQDN object cannot be used as source address of a policy. Wildcard FQDN object in object group is not supported.
- Ensure that your DNS server is stable and has a very low latency because the FQDN object in policy will rely on the results it receives.
- It is not recommended that you use FQDN object to block cloud services since multiple DNS names could resolve to the same IP address.
Comments
0 comments
Please sign in to leave a comment.