How to access a branch site network when connected to main site VPN tunnel.
Supported Devices
ATP200ATP500
ATP800
VPN50
VPN100
VPN300
USG FLEX 100W
UGS FLEX 200
USG FLEX 500
USG FLEX 700
Scenario
RoadWarrior client establishes a VPN connection with the Main Office to access resources within the main network, but also needs access to resources located on the Branch Office network. How can we make this work?
There are two ways to accomplish this, one would be for the roadwarrior client to establish a VPN connection with both locations simultaneously, but this would only be possible using a full featured VPN client such as TheGreenBow, Shrew Soft VPN Client, or other. The second option would be to use the VPN tunnel already established between the Main and Branch office(s) to push the traffic, which is what this guide covers.
Step 1:
Configure a Site-to-Site VPN connection between Main Office and Branch Office. Use the steps on this guide as a reference to establish your VPN connection.
Step 2:
Configure a Client-to-Site VPN connection between Main office and remote clients. Use the steps on the guide(s) listed below as a reference to establish your VPN connection. Select the guide below based on the VPN connection you wish to establish between the remote client and Main office.
Step 3:
Creating 'Policy Routes' to route traffic between the VPN client and Branch office. On the Main office router access menu, Configuration → Network → Routing. On the Policy Route tab click the Add button to insert a rule. We need to add a rule on the Main office router to route any traffic from the roadwarrior VPN clients destined for the Branch office network through the site-to-site VPN connection between the Main and Branch office.
Main Site
- Make sure the Enable checkbox is marked.
- Under the Criteria options, set 'Incoming' to Tunnel or SSL VPN (Tunnel if using L2TP or IPSec connection between the client and Main office. SSL VPN if the VPN connection between the client and Main office is SSL VPN.)
- Click the drop-down for 'Please select one member:' and choose the VPN rule that applies.
- For 'Source Address' select the VPN clients IP pool from the drop-down.
- For 'Destination Address' select the address object created for the Branch office IP scheme.
- Scroll down to Next-Hop and select "VPN Tunnel" from the 'Type' drop-down.
- For the 'VPN Tunnel' drop-down select the VPN rule that connects the Main office to Branch office.
- Click OK to save the settings.
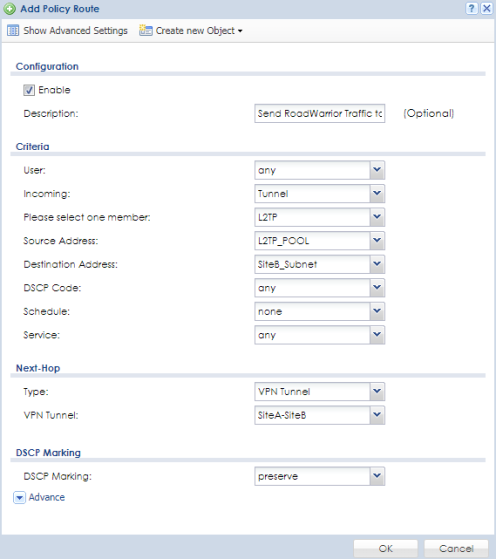
- Repeat the process to add any additional branch offices.
Branch Site
On the opposite side, the Branch Office, you will need to create a policy route rule also, so the branch knows where to send the traffic back. Add a policy route with the following settings.
- Make sure the Enable checkbox is marked.
- Under the Criteria options, set 'Incoming' to "Interface".
- Click the drop-down for 'Please select one member:' and choose Branch office internal network (LAN1, LAN2, DMZ, etc.).
- For 'Source Address' select the current LAN network from the drop-down.
- For 'Destination Address' select the address object created for the VPN client IP pool.
- Scroll down to Next-Hop and select "VPN Tunnel" from the 'Type' drop-down.
- For the 'VPN Tunnel' drop-down select the VPN rule that connects the Branch office to Main office.
- Click OK to save the settings.
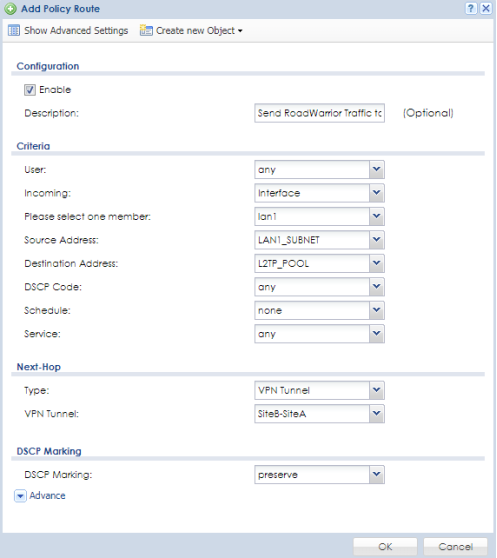
- Repeat the process on any other existing branch office(s).
Comments
0 comments
Please sign in to leave a comment.